What is AAA security? An introduction to authentication, authorisation and accounting
Authentication, authorisation and accounting (AAA) refers to a common security framework for mediating network and application access. AAA intelligently controls access to computer resources by enforcing strict access and auditing policies. This process ensures that access to network and software application resources can be restricted to specific, legitimate users.
AAA security has a part to play in almost all the ways we access networks today. Historically AAA security has set the benchmark.
Although the AAA moniker is commonly used in reference to either RADIUS or Diameter (network protocols), the concept is widely used for software application security as well. This is especially true of SaaS products and in microservice architectures.
{% include youtubePlayer.html id="qNc80H9GmeA" %}
Authentication: Who are you?
Authentication is the first step in the AAA security process and describes the network or applications way of identifying a user and ensuring the user is whom they claim to be. The user enters a valid username and password before they are granted access; each user must have a unique set of identification information. Identification can be established via passwords, single sign-on (SSO) systems, biometrics, digital certificates, and public key infrastructure.
User authentication ensures proper authorisation to access a system is granted; as data theft and information security threats become more advanced, this is increasingly important. While authentication cannot completely prevent identity theft, it can ensure network resources are protected through several authentication methods.
Upon receiving a request for access, the AAA security server compares a user's authentication credentials with other user credentials stored in the database, and if the credentials match, the user is granted access to the network or software. If the credentials are at a variance, authentication fails and user access is denied. Network and system administrators are responsible for monitoring, adding, and deleting authorised users from a system.
Once a user has been successfully authenticated, they must gain authorisation for completing certain tasks and issuing commands. Furthermore, all activity completed by that user (legitimate or otherwise), can now be logged in association with that user's authorisation credentials.
Authorisation: What resources are you permitted to use?
Authorisation refers to the process of enforcing policies, such as determining the qualities of activities, resources, or services a user is permitted to use. Authorisation usually occurs within the context of authentication; once you have been authenticated, AAA security authorisation assembles the set of attributes that describe what you are authorised to perform.
Users are assigned authorisation levels that define their access to a network and associated resources. For example, a user might be able to type commands, but only be permitted to show execute certain commands. This may be based on geographical location restrictions, date or time-of-day restrictions, frequency of logins, or multiple logins by a single user. Other types of authorisation include route assignments, IP address filtering, bandwidth traffic management, and encryption. An administrator may have privileged access, but even they may be restricted from certain actions.
For example, in more secure application architectures passwords are stored salted with no process for decrypting. These secure applications enable passwords to be changed (with existing passwords being overridden), but never retrieved.
AAA security authorisation allows you to enforce this restriction.
Accounting: What resources were accessed, at what time, by whom, and what commands were issued?
Accounting measures the resources users consume during access to a network or application, logging session statistics and user information including session duration, and data sent and received. Usage information is used for authorisation control, billing, trend analysis, resource utilisation, and capacity planning activities.
Accounting ensures that an audit will enable administrators to login and view actions performed, by whom, and at what time. One restriction of the accounting component of AAA security is that it requires an external AAA security server to store actual accounting records.
Proper accounting enables network and system administrators to review who has been attempting to access what and if access was granted.
AAA security in action
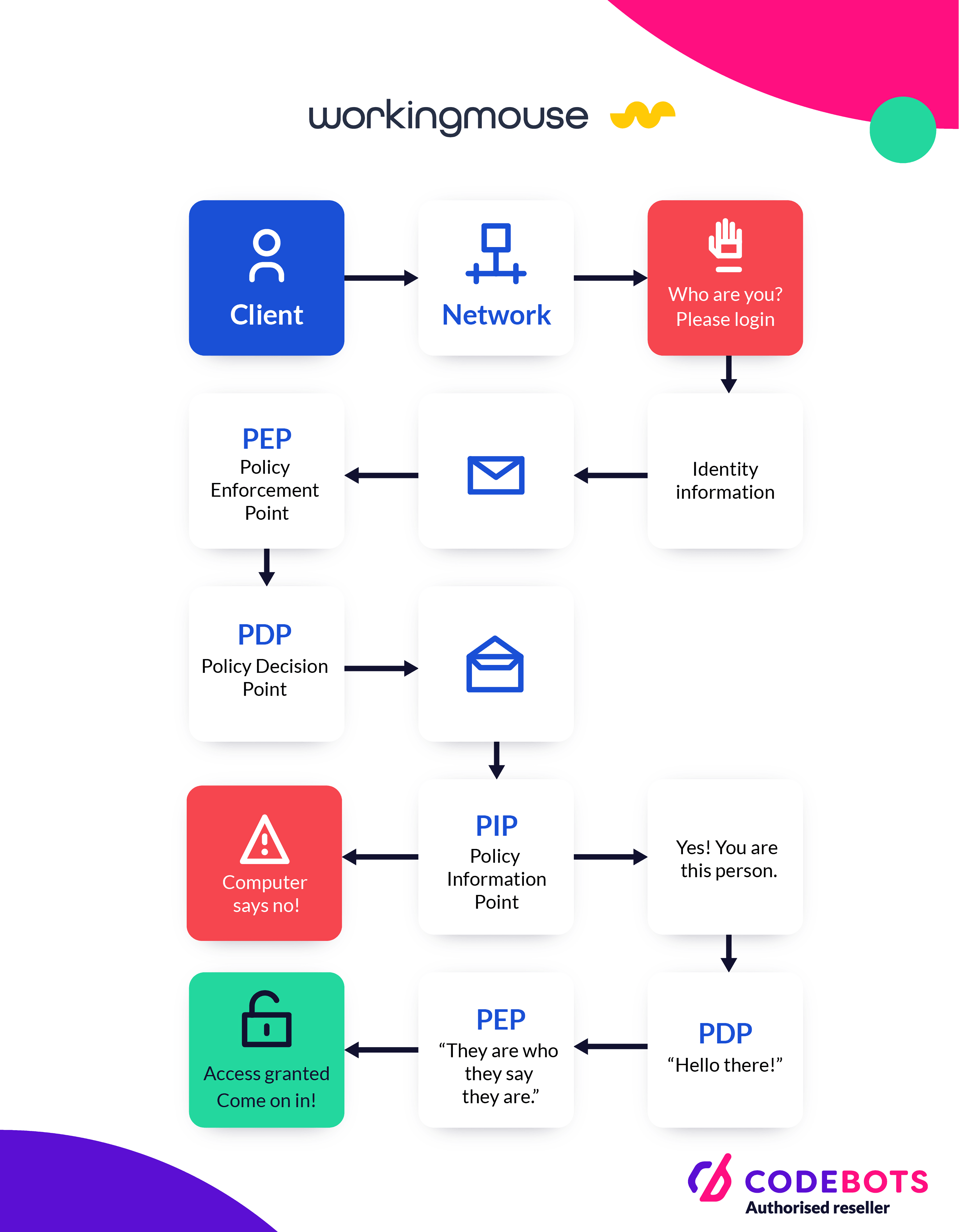
Now that you have an idea of what AAA is, let's observe at the actual process.
- A client attempts to connect to a network, and is challenged by a prompt for identify information. Identity information is sent to the Policy Enforcement Point (PEP " the authenticator), and the PEP sends the collected identity information to the Policy Decision Point (PDP " the brains), which then queries relevant information at the Policy Information Point (PIP " the information repository) to make the final access decision. The PEP cannot see the specific identity information provided, it simply relays information directly to the PDP.
- The PIP returns a success or failure measure from the credential validation assessment and sends additional information about the client to the PDP for evaluation. This may include a user's role and location.
- The PDP evaluates learned information (and any contextual information against configured policies) then makes an authorised decision. The PDP sends the PEP the authentication result, and any authorisations specific to that user, which trigger specific PEP actions that apply to the user. All information is sent to the accounting system.
- The PEP applies the authorisation profile learned from the PDP and sends an authentication successful message to the user.
- The user has system access.
Benefits of using AAA security
AAA security enables mobile and dynamic security. Without AAA security, a network must be statically configured in order to control access. IP addresses must be fixed, systems cannot move, and connectivity options must be well defined. The proliferation of mobile devices and the diverse network of consumers with their varied network access methods generates a great demand for AAA security.
AAA security is designed to enable you to dynamically configure the type of authorisation and authentication you want by creating a method list for specific services and interfaces. AAA security means increased flexibility and control over access configuration and scalability, access to standardized authentication methods such as RADIUS, TACACS+, and Kerberos, and use of multiple backup systems.
The increase of security breaches such as identity theft, indicate that it is crucial to have sound practises in place for authenticating authorised users in order to mitigate network and software security threats.
Discover More

Meet HelloWorldBot from CodeBots
HelloWorldBot provides a hands-on walkthrough of how CodeBots can turn structured thinking into real outputs. Install it from the Marketplace, follow a small example, and watch the platform capture information, automate steps, and produce versioned artefacts you can keep. It’s the simplest way to see the engine running.

The Bot Marketplace is Here
The Marketplace has landed in CodeBots Platform 6.0.0, making it easier to discover, install, and reuse bots across teams. It’s a big step toward turning scattered AI experiments into repeatable, governed outcomes.

The Vibe Coding Cliff
The vibe coding cliff is the moment the magic stops: when steering by intent and momentum no longer holds a system together and the LLM cannot keep the rising complexity in the air. It is the point where the vibes run out and real engineering has to step back in.